Visit Blue Cross' new health news site, Coverage, for compelling original reporting on health and wellness issues. Sign up to get our weekly headlines in your inbox!
Imagine opening your mail one day and getting a medical bill for a $30,000 surgery to repair a torn meniscus. But you’ve never had a torn meniscus. What happened?
You may have been a victim of medical ID theft involving your protected health information.
There were more than 300 medical/healthcare breaches involving protected health information in 2017, according to the Identity Theft Resource Center, a non-profit organization established to support victims of identity theft. That amounted to about 135,000 medical and health care records stolen, according to Experian.
In some cases, sophisticated robocalling schemes deceive people into divulging their medical information in exchange for false promises of free or discounted prescription drugs, treatment or medical equipment. An astounding 30.5 billion robocalls besieged U.S. consumers and businesses in 2017, according to the phone security company YouMail.
Callers targeting health information may claim to work for an insurer and offer free medication, DNA test kits or medical equipment in exchange for the victim’s member ID number, password, doctor’s name and other private information. Legitimate health insurers never ask for a password via text or unsolicited phone call.
“While medical identity theft is not as commonly discussed as other forms of identity theft, the consequences can be just as devastating,” said Eva Velasquez, the Identity Theft Resource Center’s CEO and president. “The repercussions can be far-reaching, including denials of medical coverage and receiving bill for procedures never performed.”
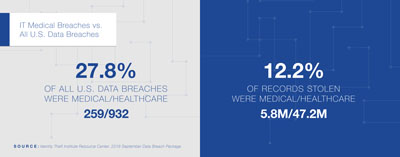
The trend shows no sign of ebbing in 2018, with 259 breaches involving medical or health information as of Sept. 30. That accounts for nearly a third of all data breaches, including the more publicized credit card and bank frauds. According to the Center’s mid-year report, a total of 3,248,545 medical and healthcare records have been breached.
“Personal health information is inherently distinct from financial information,” says Didzis Voldins, vice president and chief information security officer at Blue Cross Blue Shield of Massachusetts. “Medical information is often more robust and revealing of a person’s identity, so it is useful to criminals in many different ways. It cannot be easily erased or amended like a credit card or bank account number. This greatly complicates the effective mitigation or resolution of instances of theft and misuse.”
Health insurance information, experts say, is worth more on the dark Web’s black market – about $200 -- than even a Social Security number.
Four low-tech ways to protect yourself and your family from medical ID theft
- Hang up if you receive an unsolicited call or text asking for your insurance account’s password or other private medical information.
- Remove and dispose of labels from old prescription bottles.
- Securely shred and destroy your obsolete medical claims information or explanation of benefits.
- Do not use social media to share any future surgery or medical treatment information
- Only share your Social Security number, driver’s license or insurance card numbers with the appropriate authorities – and ask questions before you do
Ingenious criminals, naïve consumers
Sophisticated data criminals are constantly evolving their methods for attacking consumers’ security and privacy. Common tactics utilized to acquire medical information include:
- Fraudulent robocalls. Internet-powered phone systems can generate billions of illegal calls from anywhere in the world, disguising their own identity. Their schemes can lead to medical claim fraud and even the receipt of drugs or medical equipment that is not medically necessary and dangerous to use.
- Social-engineered malware. A person is tricked into visiting a website that runs a program known as a “Trojan Horse.” This program pretends to do something legitimate and asks the visitor to install a piece of malicious software which begins to syphon information from the computer’s hard drive.
- Email spear phishing, the most common threat. A person receives an email from a purportedly trusted source containing a link and asking the recipient to “click for more information” or “click to avoid IRS audit” or “click to receive your free escape to Bermuda.” By clicking, the user activates a process that scans their email account or hard drive and downloads the information.
- Dumpster diving. Believe it or not, this happens a lot. Criminals rummage through other people’s garbage or waste searching for information. Often, medical information is discarded without being properly destroyed or shredded.
- Unpatched software. Computers, laptops and handheld devices are left with outdated, vulnerable security software which can be exploited by criminals with the technical knowledge and malware to get by these unpatched security protocols.
- Social media hackers. This growing threat manifests itself as a fake friend or application install request. When users fall for this, they give access to the social media account.
In a notorious case reported by the ITRC, a substance-using pregnant woman in Utah received maternity care using another woman’s medical identity. The victim of medical ID theft received a call and visit from child protective services threatening to take away all four of her children because the baby of the fraudster had been born addicted to meth. It took a DNA test to get the victim’s name off the infant’s birth certificate and years to get her medical records straightened out.
Other criminals aim to monetize medical information by blackmailing victims over sensitive conditions, or by receiving drugs such as Oxycontin under another person’s identity and selling them in the black market.
“The value of these criminal activities adds up very quickly,” says Tim Jacobs, director of Information Security Compliance at Blue Cross Blue Shield of Massachusetts, “depending on the number of records exposed as well as myriad ways criminals can take advantage of it”.